Our Mission
Expertise We Offer
Explore our services. We specialize in innovative design and seamless connectivity. Our dedicated team ensures every project reflects your vision, integrating creativity with functionality to enhance user experience.
Network Solutions
Providing reliable networking solutions, enhancing connectivity, and streamlining communication across your business.
VPN
Optimizing your online presence through strategic SEO practices, ensuring higher visibility and increased traffic to your site.
VoIP Solutions
Crafting stunning websites tailored to your brand, ensuring an engaging user experience while maximizing functionality.
Security
Crafting stunning websites tailored to your brand, ensuring an engaging user experience while maximizing functionality.
Web Design
Crafting stunning websites tailored to your brand, ensuring an engaging user experience while maximizing functionality.
Training
Crafting stunning websites tailored to your brand, ensuring an engaging user experience while maximizing functionality.
Our Mission
Expertise We Offer
Explore our services. We specialize in innovative design and seamless connectivity. Our dedicated team ensures every project reflects your vision, integrating creativity with functionality to enhance user experience.
Network Solutions
Providing reliable networking solutions, enhancing connectivity, and streamlining communication across your business.
VPN
Optimizing your online presence through strategic SEO practices, ensuring higher visibility and increased traffic to your site.
VoIP Solutions
Crafting stunning websites tailored to your brand, ensuring an engaging user experience while maximizing functionality.
Security
Crafting stunning websites tailored to your brand, ensuring an engaging user experience while maximizing functionality.
Web Design
Crafting stunning websites tailored to your brand, ensuring an engaging user experience while maximizing functionality.
Training
Crafting stunning websites tailored to your brand, ensuring an engaging user experience while maximizing functionality.
Network Solutions
Wi-Fi 7
Old Wi-Fi 4 and 5 routers, significantly impede productivity. Wi-Fi 7 introduces
Multi-Link Operation (MLO), allowing devices to connect simultaneously using multiple Wi-Fi frequencies.
- 2.4 GHz: extended range & penetration
- 5 GHz: speed and robust connections
- 6 GHz: potentially high speeds but challenging wall penetration.
Wi-Fi 7 dynamically switches between frequencies or combines them to achieve superior speed and reliability.
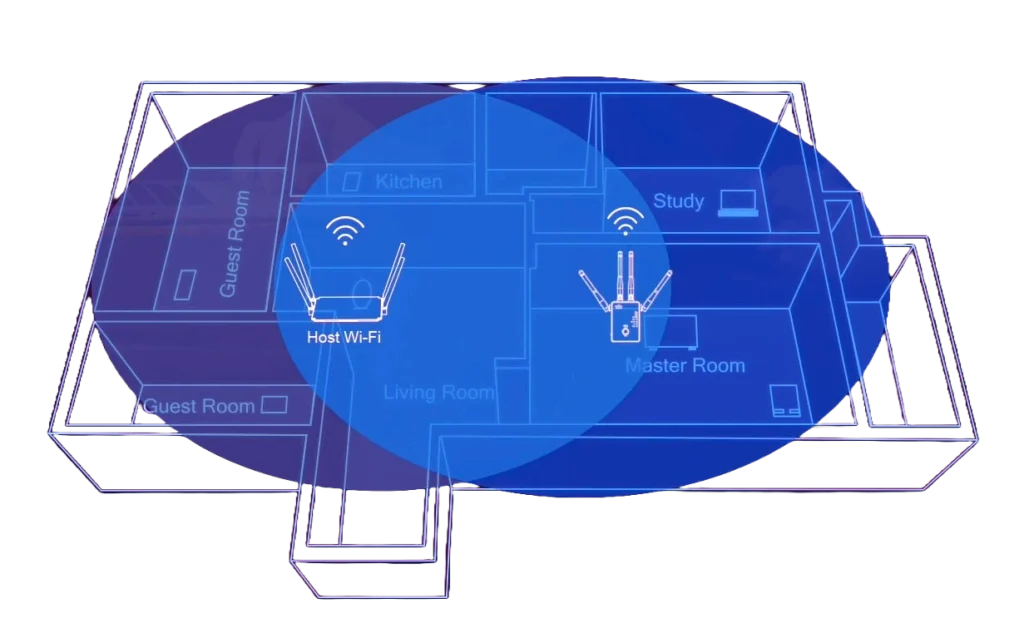
Need A Better Wireless Coverage?
Extending the Wi-Fi range in offices and homes ensures that every corner is covered, eliminating dead zones and providing consistent internet access.
A seamless roaming network is critical for users as it allows their devices to switch between different Wi-Fi access points without interruption, enhancing productivity and user experience by maintaining a stable connection as users move around.

Network Hardware
We specialize in the installation and integration of Fortinet and Ubiquiti UniFi networking equipment, offering high-performance switches and security gateways for reliable and secure data transmission.
Our solutions emphasize scalability and advanced security features to safeguard your network’s integrity while ensuring seamless connectivity and operational efficiency.



Cabling Installation
Ethernet cabling installation is a critical component in establishing a reliable and fast network connection for homes and businesses.
With proper installation, Ethernet cables can significantly enhance network speed and stability compared to wireless connections, making them ideal for environments that require high-performance networking.
Starlink
Stay Connected Anywhere
Starlink brings high-speed internet to the most remote locations, keeping you connected whether you’re camping, traveling in an RV, cruising on a boat, or living in a rural area.

Enjoy seamless streaming, gaming, and video calls no matter where your adventures take you.
We provide full installation and configuration services, so you can focus on the journey. Stay online, stay entertained, and stay productive—anytime, anywhere.


VPN
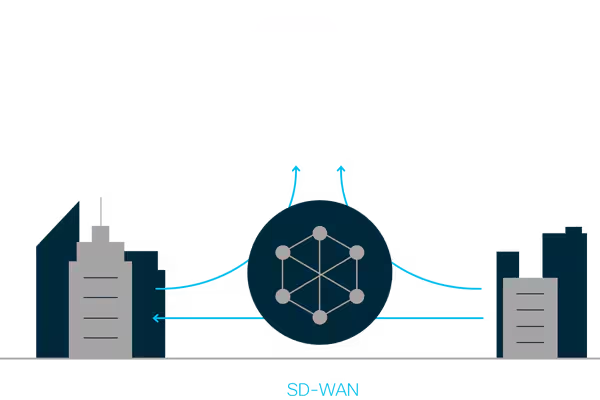
SDWan & Site-to-Site VPN
Site-to-site connections create secure network pathways between locations, while SD-WAN optimizes these connections for improved performance and cost-effectiveness.
SD-WAN dynamically chooses the best path for data based on network conditions, ensuring faster and more reliable access to applications and data.
This is useful as it allows multiple office locations to act as if they are in the same building.

Remote Access
Work from anywhere safely
Remote access VPNs are crucial for ensuring secure and private connections to home and work networks, especially in today’s increasingly digital world. They allow users to safely access and transmit sensitive information to and from external networks, protecting data from potential cyber threats.
Additionally, VPNs provide the flexibility needed for remote work by enabling employees to connect to their workplace’s network from anywhere, ensuring productivity and business continuity.

VoIP
Physical Phones
VoIP phones offer businesses a range of useful features that enhance communication efficiency and flexibility.
Their ability to operate via the internet also ensures better call quality and reliability, alongside useful data insights and analytics, making them a smarter choice for modern business environments.

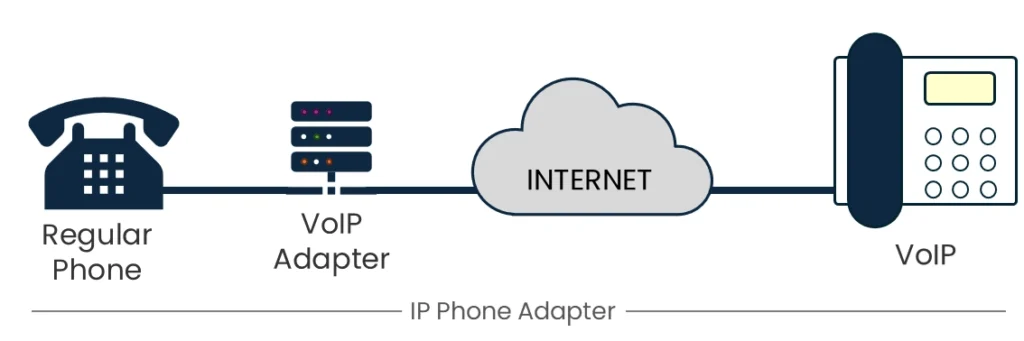
IP Phone Adapters
Use your existing phone with VoIP
Transform your traditional phone into a modern communication hub with our user-friendly VoIP adapter.
Connect your phone to the adapter, then connect it to your router. In minutes, you’ll be able to make crystal-clear internet calls.
With the help of CYBERBADGER, you can complete a full changeover to VoIP quickly and efficiently.
Bring Your Traditional Phone into the Digital Age with VOIP


Softphone
Your company phone on your mobile device
Softphones are software-based telephones that enable voice communication over the internet using a computer, tablet, or smartphone, rather than a traditional telephone device.

They are important because they offer flexibility and cost savings for businesses, allowing employees to make and receive calls from anywhere with internet access, integrating advanced features like video calling, and reducing the need for expensive hardware infrastructure.
Security
At CYBERBADGER, we help businesses stay secure with comprehensive cybersecurity solutions. Our services include risk assessment, security surveillance, system hardening, and industry best practices to safeguard your digital assets against evolving threats.
Risk Assessment
Identifying, Evaluating and Prioritizing Vulnerabilities and Threats
A Security Risk Assessment identifies, evaluates, and prioritizes threats and vulnerabilities to your organization’s assets and information.
This process enables businesses to implement effective strategies to mitigate risks, protecting against:
- Data Breaches
- Financial Losses
- Reputational Damage
Regular assessments also ensure compliance with regulations, keep security measures up-to-date against evolving threats, and foster a culture of security awareness among employees.

Security Cameras
Enhanced Security and Monitoring
Reliable security cameras are crucial for businesses and homes as they serve as a deterrent to potential intruders, reducing the likelihood of theft or vandalism.
They provide real-time monitoring, recording, and AI-enhanced capabilities, ensuring that any suspicious activity can be immediately addressed and investigated later, if necessary, which enhances the overall security and peace of mind for property owners.
Additionally, security cameras can help in providing evidence for legal proceedings or insurance claims, making them a vital component of a comprehensive security system.


Hardening & Best Practices
Hardening, baselining, and adhering to best practices are crucial for businesses and small or medium offices as they enhance security and operational efficiency.
Hardening involves securing systems by implementing the latest security measures and configurations, reducing vulnerabilities. Baselining ensures systems are in a known, secure state, facilitating the detection of unauthorized changes.
Following best practices, such as regular audits and updates, not only protects against potential threats but also optimizes performance, ensuring compliance with industry standards and building trust with clients and partners.

Website Development
In today’s digital age, having a good website is crucial for any business, whether large or small, as it serves as the primary online representation of the company.
A well-designed website can enhance brand visibility, acting as a 24/7 marketing tool that reaches potential customers worldwide. It can drive traffic through search engine optimization (SEO), where well-structured content using relevant keywords improves search rankings, making the business more discoverable.
Key components, such as a user-friendly interface, engaging content, and clear calls-to-action, are essential for attracting and retaining visitors. Additionally, responsive design ensures accessibility across devices, further broadening the potential audience and encouraging engagement and conversions.
Search Engine Optimization (SEO)

Optimize for Visibility, Stand out in the digital crowd!
At CYBERBADGER, we use proven SEO strategies to ensure your website ranks high on search engines.
From keyword optimization to technical enhancements, we help drive organic traffic to your site and attract the audience you need to grow your business.
Website Performance

Boost Performance, Maximize Impact
Slow websites lose users. Our website performance improvement services focus on speed, reliability, and user experience.
From optimizing load times to enhancing backend processes, we ensure your site delivers peak performance for every visitor.
Content Management Systems (CMS)




Your CMS, Your Choice
Flexibility matters. Whether it’s WordPress, Shopify, Wix, or Squarespace, we work with leading content management systems to build and customize websites tailored to your needs. Manage your content effortlessly with the platform that best fits your business
Security Training
Security training is crucial for any company to safeguard its operations and data against various cyber threats. By fostering phishing awareness, employees become adept at identifying and avoiding fraudulent communications that could compromise sensitive information.
Moreover, training on password management ensures that staff utilize strong, unique passwords that protect access to corporate systems and data. By implementing security best practices through regular education, companies can significantly reduce the risk of data breaches, thus safeguarding their reputation and ensuring compliance with regulatory requirements.

Phishing Awareness
Don't Take the Bait!
Phishing attacks are the gateway to data breaches and financial losses. Our interactive phishing awareness training equips your team with the skills to recognize and avoid deceptive emails, fake websites, and other traps set by cybercriminals.
Stay ahead of the threats and protect your organization—because a vigilant team is your best defense!
Password Management
Lock Down Your Security!
Strong passwords are the first line of defense against cyber threats. Our password management training teaches your team how to create, store, and manage secure passwords effectively.
Learn best practices, avoid common pitfalls, and embrace tools that simplify security without compromising convenience.
Safeguard your digital assets—one password at a time!
Password: ********
Secure Browsing
Browse Smart, Stay Safe!
The internet is a treasure trove of information—but also a minefield of risks. Our safe browsing training helps you identify trustworthy websites, spot malicious links, and evaluate online resources with confidence.
Learn how to navigate the web securely and make informed decisions to protect your personal and organizational data.


